Have I Been Pwned: The Complete Guide to Understanding and Taking Action in 2025

Loading...

In today's digital landscape, data breaches have become alarmingly common. With billions of records exposed annually, the question isn't if your data will be compromised, but when. Have I Been Pwned (HIBP) serves as an essential early warning system for digital identity protection. This free service helps you discover if your personal information has been exposed in known data breaches, empowering you to take action before your compromised data leads to serious consequences. Understanding Have I Been Pwned is crucial for anyone concerned about their online security.
This comprehensive guide explores what Have I Been Pwned is, how to use it effectively, and most importantly, what specific actions to take based on different breach scenarios. We'll also examine how Have I Been Pwned fits into a broader security strategy and why regular breach monitoring through Have I Been Pwned should be part of everyone's digital hygiene routine. Whether you're a security novice or an experienced professional, this guide will help you leverage Have I Been Pwned to better protect your digital identity.
Have I Been Pwned is a free service created by renowned cybersecurity expert Troy Hunt that allows users to check if their personal data has been compromised in known data breaches. The term "pwned" (pronounced "poned") originated as gamer slang for "owned" or "defeated," but in cybersecurity contexts, being "pwned" means your data has been compromised. The Have I Been Pwned service aggregates data from publicly disclosed breaches, creating a searchable database that individuals can use to discover if their information has been exposed.
Troy Hunt, an Australian web security consultant and Microsoft Regional Director, established Have I Been Pwned in 2013 after analyzing data from multiple large-scale breaches. The service has since grown to become one of the most trusted and comprehensive breach notification platforms available. Have I Been Pwned operates on principles of transparency and security, providing an invaluable resource for millions of users worldwide. The core mission of Have I Been Pwned is to make data breach information more accessible to ordinary users.
Have I Been Pwned continuously adds new breach data as it becomes publicly available, ensuring users have access to the most current information about their potential exposure. The database currently contains billions of compromised accounts from thousands of different data breaches. Beyond individual users, Have I Been Pwned also offers services for organizations to monitor domain-wide email addresses for potential breaches. Understanding how Have I Been Pwned works is the first step toward better protecting your digital information.

Using Have I Been Pwned is straightforward, but understanding how to interpret and act on the results requires some knowledge. The primary features of Have I Been Pwned are email checking, password checking, and domain monitoring for businesses. Let's explore how to use each of these Have I Been Pwned functions effectively.
The most common way to use Have I Been Pwned is to check if your email address appears in any known data breaches:
If Have I Been Pwned shows your email has been compromised, don't panic. The results page will display which breaches your email appeared in, when they occurred, and what types of data were exposed. This information is crucial for determining your appropriate response. Have I Been Pwned makes this process simple enough for anyone to perform regular checks on their email addresses.
For more comprehensive protection, Have I Been Pwned offers a notification service. By subscribing, you'll receive automatic alerts whenever your email address appears in newly added breaches. This proactive approach using Have I Been Pwned ensures you're informed about new exposures without having to manually check the site regularly.
Have I Been Pwned also provides a "Pwned Passwords" feature that lets you check if specific passwords have appeared in data breaches:
This password check is performed securely using k-anonymity, meaning your full password is never sent to Have I Been Pwned servers. Instead, only a partial hash of your password is transmitted, maintaining your security while still allowing the system to check against the database of compromised passwords. If Have I Been Pwned indicates your password has been exposed, you should change it immediately on all services where it's used.
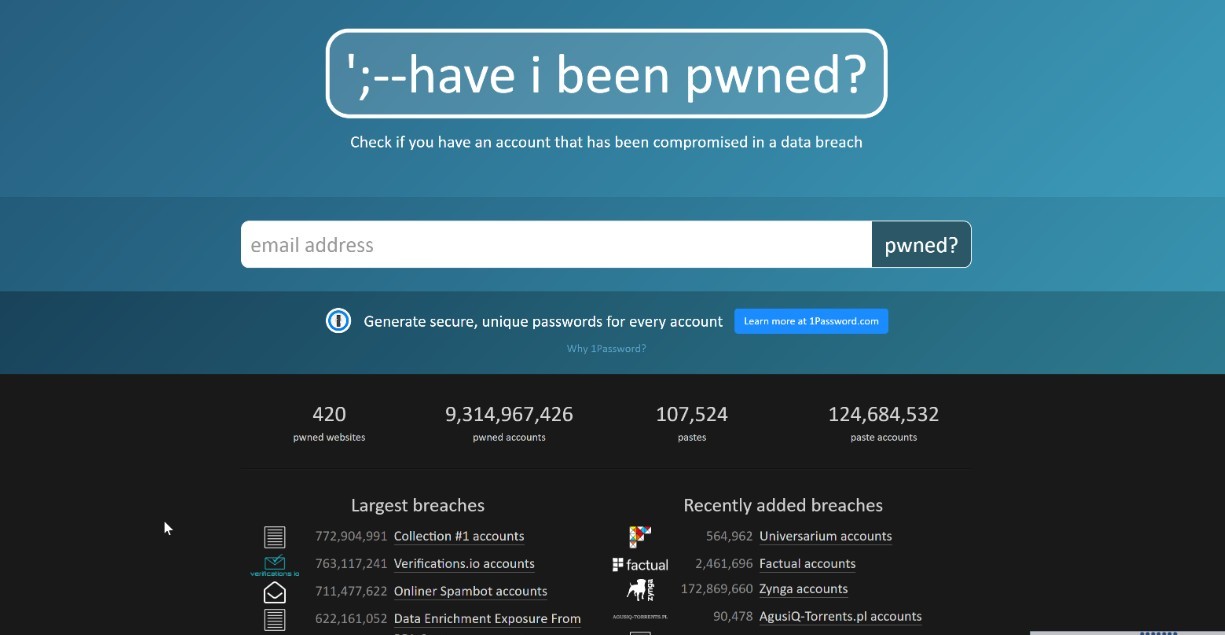
When Have I Been Pwned shows you've been "pwned," understanding the specific implications is critical for taking appropriate action. Different types of breaches carry different risks, and Have I Been Pwned provides valuable context about each breach to help you assess the potential impact. Interpreting Have I Been Pwned results correctly allows you to prioritize your response actions.
Have I Been Pwned results provide details about each breach, including:
Have I Been Pwned categorizes breaches as either "verified" or "unverified," with verified breaches having been confirmed through reliable sources. Additionally, Have I Been Pwned marks some breaches as "sensitive," typically indicating breaches from adult websites or dating services that might contain particularly embarrassing or damaging personal information.
Different data types reported by Have I Been Pwned present different levels of risk:
Understanding which data types were exposed in each breach reported by Have I Been Pwned helps determine the severity of the risk and informs what protective measures you should take. The more sensitive the exposed information reported by Have I Been Pwned, the more aggressive your response should be.
After checking Have I Been Pwned, your next steps should be determined by what information was exposed. Different exposure scenarios require different responses. Have I Been Pwned provides the information you need to create an appropriate action plan based on breach severity. Here are recommended response plans for different levels of exposure identified by Have I Been Pwned.
If Have I Been Pwned shows only your email address was exposed:
Email-only exposures reported by Have I Been Pwned present the lowest risk but still warrant increased awareness. While no immediate password changes are necessary, these breaches often lead to increased targeting for phishing attacks attempting to capture your credentials. Remaining alert after an email exposure on Have I Been Pwned is your best defense.
When Have I Been Pwned shows both email and password were compromised:
Password exposures identified by Have I Been Pwned require immediate action. The greatest risk comes from password reuse across multiple services, as attackers often try exposed credentials on popular websites. Implementing unique passwords for each service prevents a single breach from compromising multiple accounts. Have I Been Pwned notifications can alert you to future exposures.
For breaches containing significant personal identifiable information (PII) reported by Have I Been Pwned:
When Have I Been Pwned reveals extensive personal data exposure, comprehensive protection measures become necessary. This level of breach significantly increases your risk of identity theft and financial fraud. Taking decisive action promptly after discovering such an exposure on Have I Been Pwned can prevent more serious consequences.
Learning from Have I Been Pwned that your data has been breached can trigger anxiety, shame, or helplessness. These emotional responses are normal but understanding some key facts can help maintain perspective:
Rather than viewing a positive result on Have I Been Pwned as a failure, see it as an opportunity to strengthen your security posture. Have I Been Pwned provides the awareness needed to take protective action before exposed data leads to actual harm. The emotional impact of discovering breaches through Have I Been Pwned should motivate improvement rather than cause paralysis.
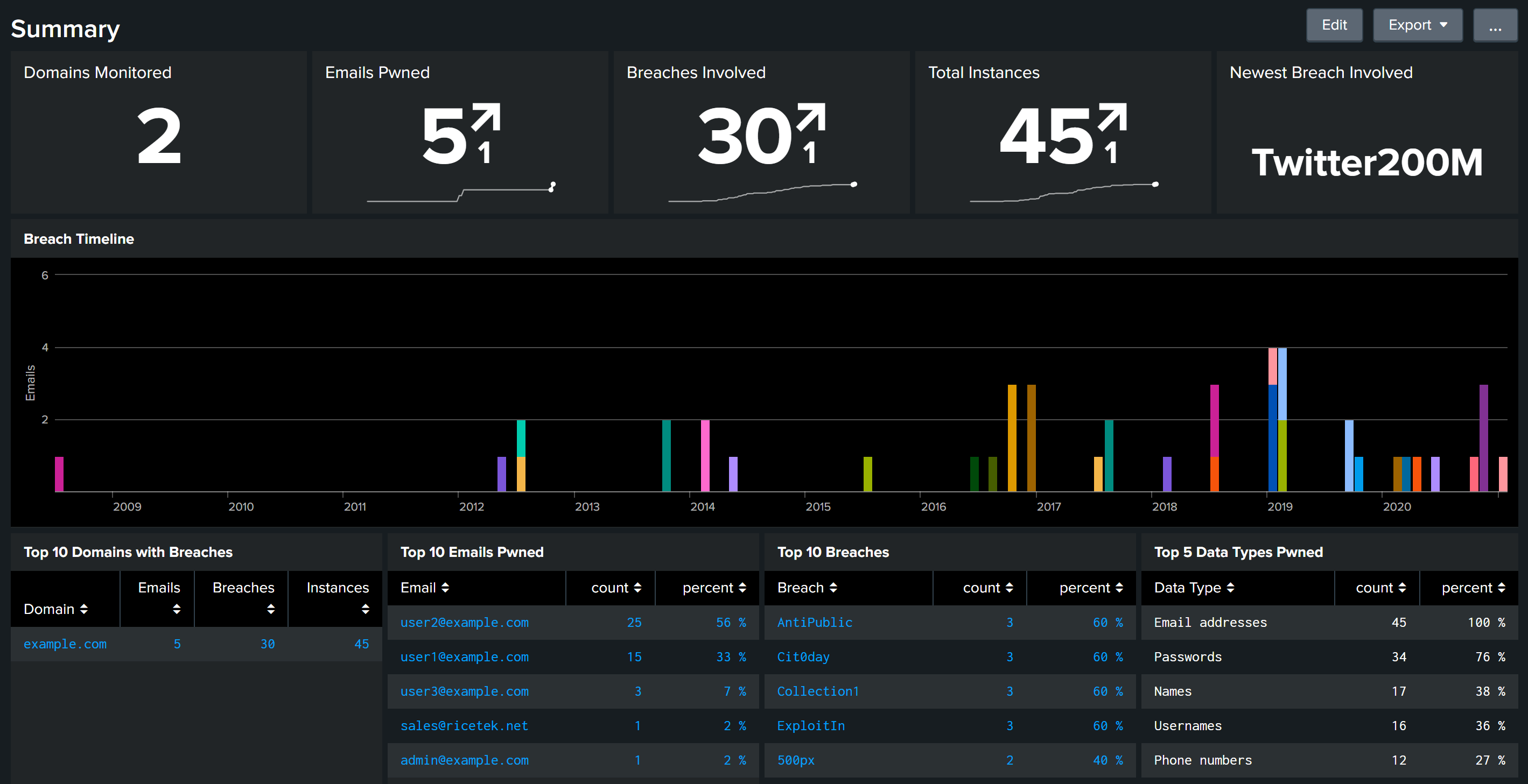
Have I Been Pwned offers domain search functionality for organizations seeking to protect their corporate digital assets and employee information. This business-focused aspect of Have I Been Pwned provides valuable threat intelligence for companies of all sizes. Implementing Have I Been Pwned monitoring at the organizational level should be part of any comprehensive security program.
To use Have I Been Pwned for business protection:
Business domain monitoring through Have I Been Pwned helps security teams identify compromised employee credentials before they lead to security incidents. Many data breaches begin with credential stuffing attacks using previously exposed passwords, making Have I Been Pwned an essential early warning system for organizations. Integrating Have I Been Pwned into corporate security processes creates an additional layer of protection.
While Have I Been Pwned is an invaluable security tool, understanding its limitations is important:
Have I Been Pwned should be viewed as one component of a comprehensive security strategy rather than a complete solution. The service provides excellent historical breach data but cannot protect against future breaches or detect breaches that haven't been publicly disclosed. Using Have I Been Pwned regularly is important, but it shouldn't be your only security measure.
While Have I Been Pwned provides valuable breach information, complete digital protection requires additional measures. Use these Have I Been Pwned-informed strategies for better security:
Have I Been Pwned works best when integrated into this broader security approach. The service provides the critical function of breach awareness, but preventing future compromises requires implementing strong security practices across all your digital activities. Regular checks with Have I Been Pwned combined with these protective measures create a robust defense against the consequences of data breaches.
Is Have I Been Pwned safe to use? Yes, Have I Been Pwned is considered highly trustworthy in the security community. The service was created by respected security researcher Troy Hunt and uses secure methods to check your information against breach data.
How often should I check Have I Been Pwned? It's recommended to check Have I Been Pwned monthly or set up automatic notifications to receive alerts whenever your email appears in new breaches.
What if Have I Been Pwned shows I'm in a breach from years ago? Even old breaches warrant attention. If you haven't changed the affected passwords since the breach date shown by Have I Been Pwned, you should do so immediately.
Can Have I Been Pwned tell me if my accounts are currently hacked? No, Have I Been Pwned only shows if your information appeared in known historical data breaches. It cannot detect current unauthorized access to your accounts.
Have I Been Pwned provides an essential service for anyone concerned about their digital security. By regularly checking your email addresses and passwords against the Have I Been Pwned database, you can discover if your information has been compromised and take appropriate action before serious harm occurs.
The digital landscape continues to evolve, with data breaches becoming larger and more frequent. Services like Have I Been Pwned empower individuals to take control of their digital security through awareness and informed action. Incorporating Have I Been Pwned checks into your security routine represents a proactive approach to protecting your digital identity.
Remember that finding yourself "pwned" isn't a failure—it's an opportunity to strengthen your security posture. By understanding Have I Been Pwned results and implementing the appropriate response strategies, you can significantly reduce your risk and maintain better control over your personal information in an increasingly vulnerable digital world.
Looking for more email troubleshooting and management guidance? Check out these related articles:
Master your startup journey with our comprehensive guide. Learn the essential startup journey stages, overcome common startup journey challenges, and develop the startup journey mindset needed to transform your idea into a successful business exit through strategic startup journey planning.
📖 Guides
Master AI development with our comprehensive guide. Learn frameworks, tools, best practices, and implementation strategies for building powerful AI applications from concept to deployment.
📖 Guides
Master AI communication with our comprehensive guide. Learn about AI communication technologies, AI communication implementation strategies, AI communication applications, AI communication benefits, AI communication challenges, and AI communication future trends for businesses and individuals seeking AI communication excellence.
📖 Guides