The Ultimate Guide to Email Security: Protect Your Business in 2025

Loading...

In today's digital landscape, email security has become one of the most critical aspects of cybersecurity for businesses of all sizes. With cybercriminals increasingly targeting email systems through sophisticated attacks, implementing robust protection measures is no longer optional—it's essential for business survival. Email security encompasses a comprehensive approach to protecting email communications from unauthorized access, data breaches, and malicious attacks.
This ultimate guide to email security provides everything you need to know about protecting your organization's email infrastructure. From understanding the latest threats to implementing advanced security solutions, this guide will help you build a fortress around your email communications. Whether you're a small business owner or an enterprise security professional, mastering these protection strategies is crucial for protecting sensitive information and maintaining business continuity.
The importance of email security cannot be overstated in our interconnected world. With email serving as the primary communication channel for most businesses, it has become the preferred attack vector for cybercriminals. Effective protection strategies can prevent data breaches, protect customer information, and save organizations millions in potential damages and regulatory fines.
Email security refers to the collective measures, protocols, and technologies designed to protect email accounts and communications from unauthorized access, loss, or compromise. Modern email security solutions go beyond simple spam filtering to provide comprehensive protection against sophisticated cyber threats that target email systems.
The foundation of effective protection lies in understanding that email communications are inherently vulnerable. Traditional email protocols were not designed with security in mind, making email security enhancements essential for protecting sensitive business communications. Today's email security threat landscape requires a multi-layered approach that addresses threats at every level of email communication.
Key components of comprehensive email security include:
The business impact of inadequate protection can be devastating. Organizations without proper email security measures face increased risks of data breaches, financial losses, and reputational damage. Studies show that email-based attacks account for over 90% of successful cyber breaches, highlighting the critical importance of robust email security implementations.
Effective protection strategies safeguard more than just email communications—they protect entire business ecosystems. When email security is properly implemented, it creates a protective barrier that prevents cybercriminals from accessing sensitive data, disrupting operations, or compromising customer trust.
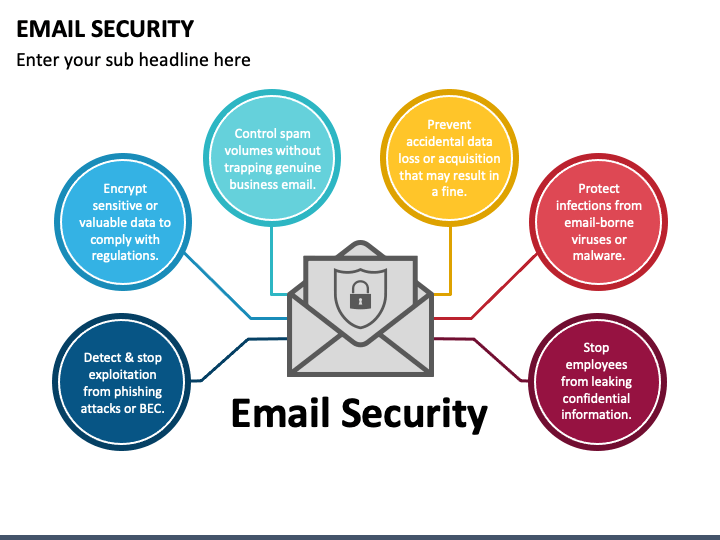
The threat landscape continues to evolve rapidly, with cybercriminals developing increasingly sophisticated attack methods that challenge traditional email security defenses. Understanding these threats is essential for implementing effective protection strategies that can adapt to emerging risks.
Phishing remains the most prevalent threat to email security, with attackers using increasingly sophisticated techniques to bypass security filters. Modern phishing attacks targeting email systems include spear phishing, whaling attacks, and business email compromise (BEC) schemes that can devastate organizations lacking proper protection measures.
Advanced phishing techniques challenging email security:
BEC attacks represent one of the most financially damaging threats to email security systems. These sophisticated attacks bypass traditional email security measures by impersonating trusted executives or vendors to request fraudulent wire transfers or sensitive information. Effective email security solutions must include advanced authentication and verification mechanisms to prevent BEC attacks.
Email-delivered malware continues to challenge email security systems, with ransomware attacks causing billions in damages annually. Modern email security protection solutions must detect and block sophisticated malware that uses advanced evasion techniques to bypass traditional security filters.
Insider threats and accidental data leaks pose significant challenges to email security organizations. Companies need email security solutions that can monitor outbound communications and prevent sensitive data from leaving the organization through email channels.
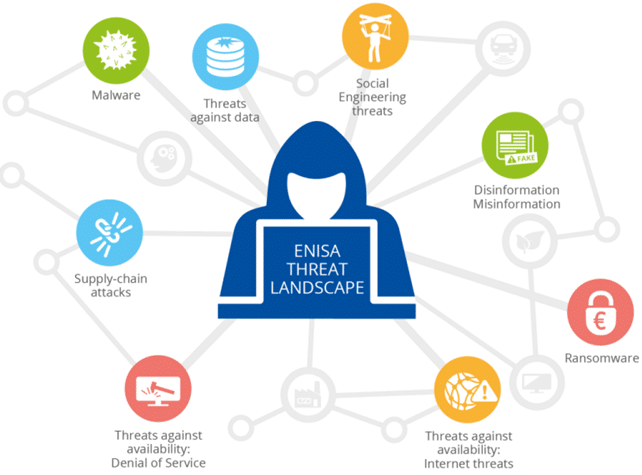
Implementing effective email security requires a multi-layered approach that combines various technologies and solutions. Modern security architectures integrate multiple protection mechanisms to create comprehensive defense systems that can address diverse threat vectors.
Secure Email Gateways serve as the first line of defense in protection architectures. These solutions scan incoming and outgoing emails for threats, using advanced detection engines to identify and block malicious content before it reaches users. Leading gateways incorporate machine learning and AI to improve threat detection accuracy.
Key features of advanced email security gateways:
Email authentication protocols form the backbone of modern email security strategies. These protocols verify the authenticity of email senders and help prevent spoofing attacks that can compromise communications. Implementing proper email authentication is essential for maintaining security and deliverability.
Essential email authentication protocols:
SPF (Sender Policy Framework): Defines authorized sending IP addresses for domains, helping security systems verify legitimate senders and reject spoofed emails.
DKIM (DomainKeys Identified Mail): Adds cryptographic signatures to emails, enabling email security systems to verify message integrity and sender authenticity.
DMARC (Domain-based Message Authentication, Reporting & Conformance): Provides policy framework for handling authentication failures, giving organizations control over their security posture.
Encryption represents a critical component of comprehensive email security strategies. Modern solutions offer multiple encryption options to protect sensitive communications both in transit and at rest.
Types of email encryption for email security:
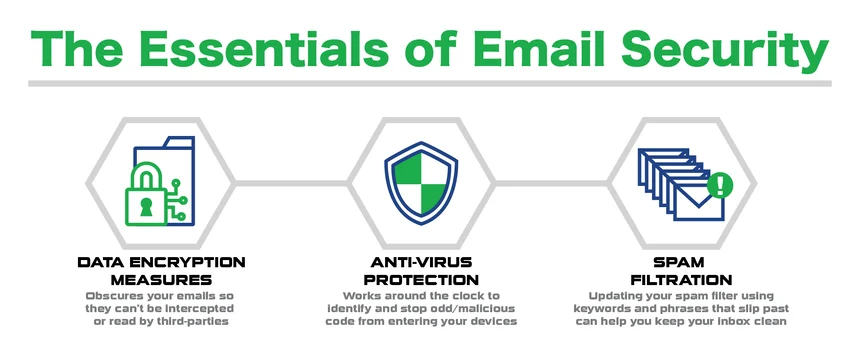
The future of email security lies in advanced technologies that can adapt to evolving threats and provide proactive protection. Modern solutions leverage artificial intelligence, machine learning, and behavioral analysis to detect and prevent sophisticated attacks that traditional methods might miss.
Artificial intelligence is revolutionizing email security by enabling systems to learn from attack patterns and adapt to new threats automatically. AI-powered solutions can analyze vast amounts of data to identify subtle indicators of compromise that human analysts might overlook.
AI capabilities enhancing email security:
Machine learning algorithms continuously improve email security effectiveness by learning from new threats and attack patterns. These email security systems enhance protection by reducing false positives while improving detection rates for sophisticated attacks.
Zero Trust principles are transforming email security architectures by assuming that no communication is inherently trustworthy. Zero Trust email security models verify every email and user interaction, providing enhanced protection against both external threats and insider risks.
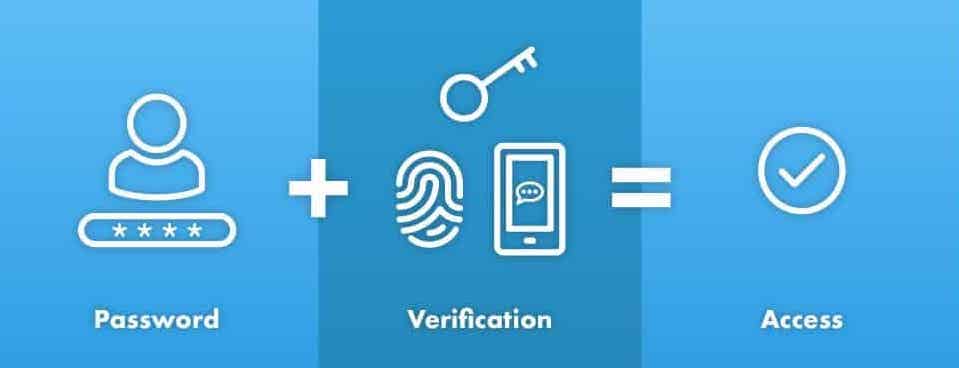
Strong authentication mechanisms are fundamental to effective email security strategies. Multi-factor authentication (MFA) significantly enhances email security protection by requiring multiple verification factors before granting access to email systems.
MFA implementation should be a priority for any organization serious about email security. Modern email security strategies incorporate various authentication factors including something you know (passwords), something you have (tokens), and something you are (biometrics).
Advanced email security implementations use conditional access policies that evaluate risk factors before granting email access. These policies enhance security by considering factors like location, device type, and user behavior patterns.
Data Loss Prevention (DLP) technologies play a crucial role in modern email security strategies by monitoring and controlling sensitive data movement through email channels. Effective implementations include comprehensive DLP capabilities that prevent accidental or intentional data leaks.
Modern solutions integrate DLP capabilities to scan outbound emails for sensitive information like credit card numbers, social security numbers, and proprietary data. These features help organizations maintain compliance and protect sensitive information.
Implementations must address various regulatory requirements including GDPR, HIPAA, SOX, and industry-specific standards. Compliance-focused email security solutions provide audit trails, retention policies, and privacy controls required by regulatory frameworks.
Key compliance features in email security:
Successful implementations require more than just technology—they need comprehensive strategies that address people, processes, and technology. Following email security best practices ensures that organizations maximize their security investments and minimize risk exposure.
Human factors represent the weakest link in many security implementations. Comprehensive strategies include regular user training and awareness programs that help employees recognize and respond appropriately to email threats.
Essential email security training topics:
Organizations need clear policies that define acceptable use, security requirements, and incident response procedures. Well-defined email security policies provide the foundation for consistent security practices across the organization.
Ongoing assessments help organizations identify vulnerabilities and improve their security posture. Regular audits should evaluate technical controls, policy compliance, and user awareness levels.
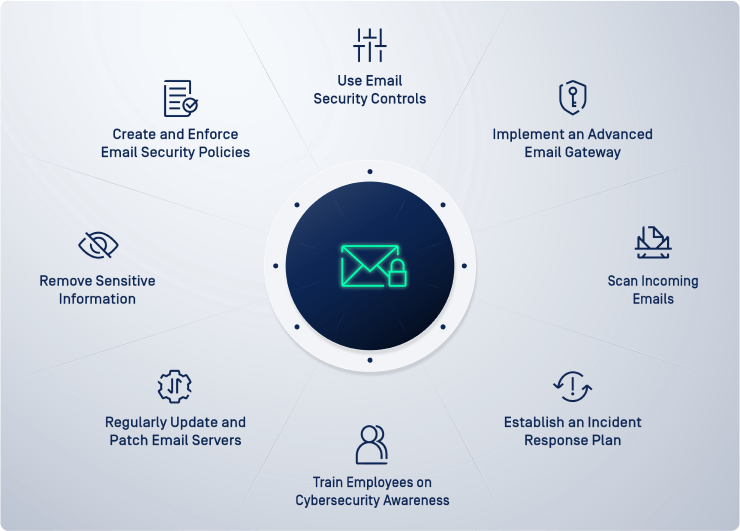
Even with robust email security measures in place, organizations must be prepared to respond to security incidents. Effective strategies include comprehensive incident response plans that minimize damage and enable rapid recovery from attacks.
Continuous monitoring is essential for effective incident response. Modern solutions provide real-time alerting and automated response capabilities that help organizations detect and respond to threats quickly.
When security incidents occur, organizations need forensic capabilities to understand the scope and impact of attacks. Advanced solutions provide detailed logging and analysis tools that support incident investigation and legal requirements.
Incident response plans must include recovery procedures that restore normal operations quickly while preventing reinfection. Business continuity planning ensures that email communications can continue even during security incidents.
The security landscape continues evolving with new technologies and threat vectors. Understanding future trends helps organizations prepare for emerging challenges and opportunities in email protection.
Cloud-based solutions offer scalability, flexibility, and advanced capabilities that traditional on-premises systems cannot match. The future of email protection lies in cloud-native architectures that can adapt quickly to new threats.
Modern solutions increasingly rely on API integrations that enable seamless connectivity with other security tools and business applications. API-based architectures provide greater flexibility and customization options.
As quantum computing advances, email security solutions must prepare for quantum-resistant encryption methods. Future implementations will need to incorporate post-quantum cryptography to maintain long-term protection.
Organizations need metrics to evaluate the effectiveness of their security investments and identify areas for improvement. Comprehensive measurement programs track both technical metrics and business outcomes.
Effective measurement includes both technical and business metrics that demonstrate the value of security investments. Organizations should track metrics like threat detection rates, false positive rates, and incident response times.
Essential email security metrics:
Calculating return on investment for security helps organizations justify security spending and optimize their security portfolios. Email security ROI calculations should consider both direct costs and avoided losses from prevented attacks.
Selecting appropriate solutions requires careful evaluation of organizational needs, technical requirements, and budget constraints. The market offers diverse options ranging from basic spam filtering to comprehensive security platforms.
When evaluating vendors, organizations should consider factors like detection accuracy, ease of management, integration capabilities, and support quality. The best solutions provide comprehensive protection while minimizing administrative overhead.
Successful implementations require careful planning that addresses technical, operational, and organizational factors. Implementation plans should include migration strategies, user training, and performance monitoring.
Security investments should be viewed as business enablers rather than just cost centers. Organizations should consider the total cost of ownership including licensing, implementation, and ongoing management costs when budgeting for protection.
Email security represents one of the most critical investments organizations can make in their cybersecurity posture. With email serving as the primary attack vector for cybercriminals, implementing comprehensive email security measures is essential for protecting sensitive data, maintaining business continuity, and preserving customer trust.
The key to successful email security lies in adopting a multi-layered approach that combines advanced technology with strong policies and user education. Organizations that invest in comprehensive security solutions and follow best practices significantly reduce their risk of successful cyber attacks and data breaches.
As the threat landscape continues evolving, security strategies must adapt to address new challenges and opportunities. By staying informed about emerging threats and technologies, organizations can maintain effective protection postures that safeguard against both current and future risks.
The investment in robust email security pays dividends through reduced risk exposure, improved compliance posture, and enhanced business resilience. Organizations that prioritize email protection position themselves for success in an increasingly dangerous cyber environment.
Ready to strengthen your email security? Start by assessing your current security posture and identifying areas for improvement. The right email security strategy can transform your organization's security posture and provide peace of mind in today's threat-filled digital landscape.
Q: What are the most important components of email security? A: The most critical components include secure email gateways, email authentication protocols (SPF, DKIM, DMARC), encryption, multi-factor authentication, and user awareness training. Comprehensive protection requires a multi-layered approach addressing all potential attack vectors.
Q: How much should organizations budget for email security? A: Security budgets typically range from $2-10 per user per month for basic protection to $15-50+ for enterprise-grade solutions. Organizations should consider email security as a critical business investment rather than just an IT expense, factoring in potential breach costs when budgeting.
Q: Can small businesses implement effective email security? A: Yes, small businesses can achieve excellent protection through cloud-based solutions that provide enterprise-grade protection at affordable prices. Many vendors offer scalable solutions specifically designed for small and medium businesses.
Q: How often should email security policies be updated? A: Security policies should be reviewed and updated at least annually, or whenever significant changes occur in the threat landscape, technology infrastructure, or regulatory requirements. Regular policy updates ensure measures remain effective and relevant.
Q: What is the biggest email security mistake organizations make? A: The biggest mistake is relying solely on technology without addressing the human factor. Effective protection requires comprehensive user training and awareness programs, as human error accounts for the majority of successful email-based attacks.
Q: How can organizations measure email security effectiveness? A: Effectiveness can be measured through metrics like threat detection rates, false positive rates, incident response times, and user awareness scores. Organizations should also conduct regular assessments and penetration testing to identify vulnerabilities.
Q: What role does AI play in modern email security? A: AI enhances email security through advanced threat detection, behavioral analysis, and automated response capabilities. AI-powered solutions can identify sophisticated attacks that traditional rule-based systems might miss, while reducing false positives and improving overall security effectiveness.
Looking for more email troubleshooting and management guidance? Check out these related articles:
Master business productivity with our comprehensive guide. Learn proven strategies, essential tools, and best practices to boost efficiency, increase profitability, and achieve sustainable growth.
📖 Guides
Discover the complete guide to email templates. Learn how to create, customize, and optimize email templates for sales, marketing, and customer service to save time and boost engagement.
📖 Guides
Master your startup journey with our comprehensive guide. Learn the essential startup journey stages, overcome common startup journey challenges, and develop the startup journey mindset needed to transform your idea into a successful business exit through strategic startup journey planning.
📖 Guides